
Introduction To Cyber Crime as a Service
In today’s digital age, technology and the internet have become an integral part of our lives. However, this increasing reliance on technology has also opened the doors to a new and dangerous phenomenon known as “Cyber Crime as a Service.” This term refers to a model where cyber criminal tools, services, and expertise are made available to individuals or groups for a fee or subscription. It has democratised cyber crime, making it accessible to anyone with the financial means, regardless of their technical skills.
Example 1: Ransomware as a Service
Ransomware as a Service is a prevalent form of Cyber Crime as a Service. This service model empowers individuals to initiate ransomware attacks without developing their own malicious software. Providers furnish customisable and deployable ready-made ransomware. Typically, in this arrangement, users allocate a portion of the ransom payment to the service provider, establishing a profitable relationship for both.
Ransomware attacks usually entail encrypting essential files on a victim’s system, followed by a demand for ransom in return for the decryption key. This form of attack has gained traction in recent years, resulting in numerous high-profile incidents, including the WannaCry attack affecting thousands of organisations worldwide.
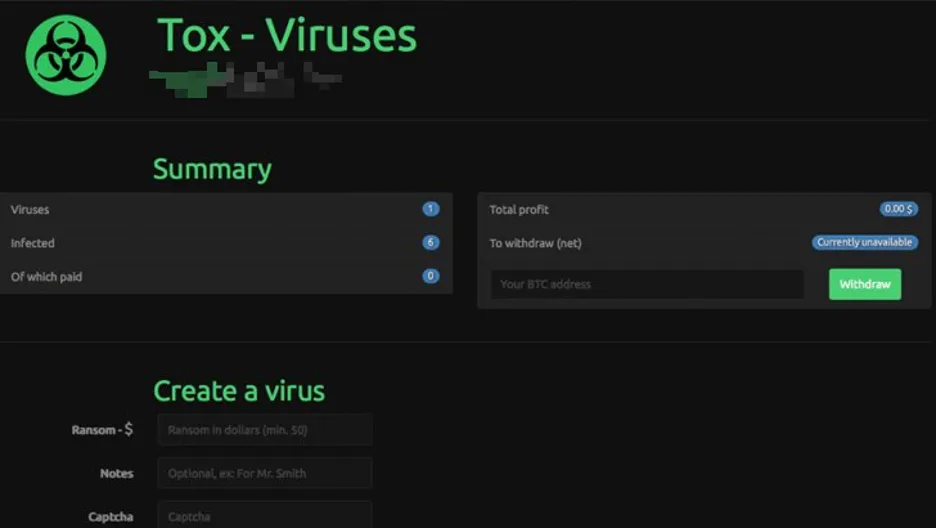 Photo: An image showcasing Tox, a prominent Ransomware as a Service provider
Photo: An image showcasing Tox, a prominent Ransomware as a Service provider
One notable provider can be viewed above. Tox boasts a user-friendly interface, round-the-clock technical support, and a suite of features that facilitate the initiation of ransomware attacks. With Tox, individuals, regardless of their technical expertise, have the potential to engage in cyber crime.
Example 2: Distributed Denial of Service as a Service
Distributed Denial of Service (DDoS) as a Service is another prevalent form of Cyber Crime as a Service. This service enables users to inundate a target’s online services with traffic, potentially leading to system overwhelm. It is commonly used for extortion or securing a competitive edge. Users can easily commission DDoS attacks by paying a fee, thereby eliminating the need for specialised knowledge or resources.
DDoS attacks aim to disrupt the availability of websites or online services by saturating them with excessive traffic, rendering them unreachable for legitimate users. Such attacks can inflict significant damage on organisations that depend on their online presence for revenue generation or customer service.
DDoS as a service has a long history, initially originating as “booters” or stress flooding tools. Potential customers can register on a web portal and opt for a monthly subscription, with rates ranging from $7.00 all the way to $120.00.
After a package has been taken out, users can simply input the victim’s IP address and chosen port, resulting in an overwhelming influx of traffic to the specified IP address.
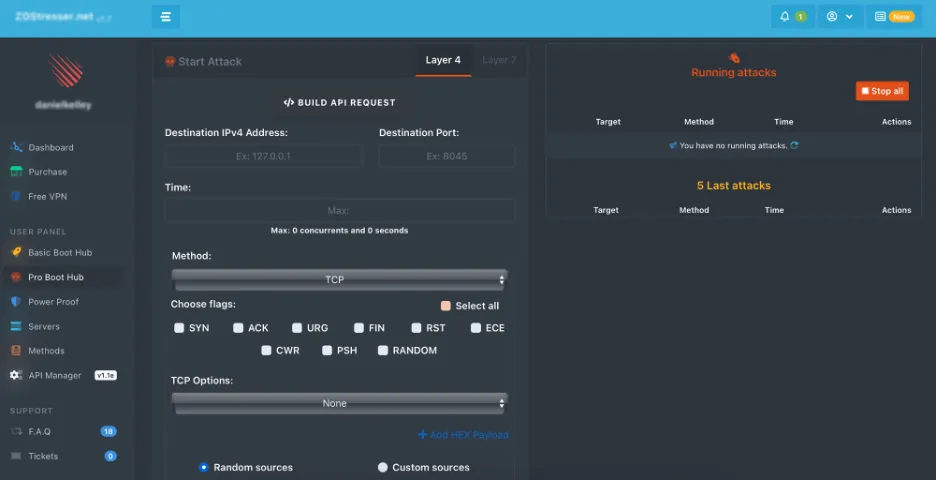
Photo: An image displaying the interface for a typical booter
Referring to the screenshot above, you can observe an example of what a typical “booter” panel looks like, which one can access for a monthly fee.
Conversely, there are services like the one highlighted below, which adopt a more hands-on approach, allowing you to pay an individual or group to take a network offline.
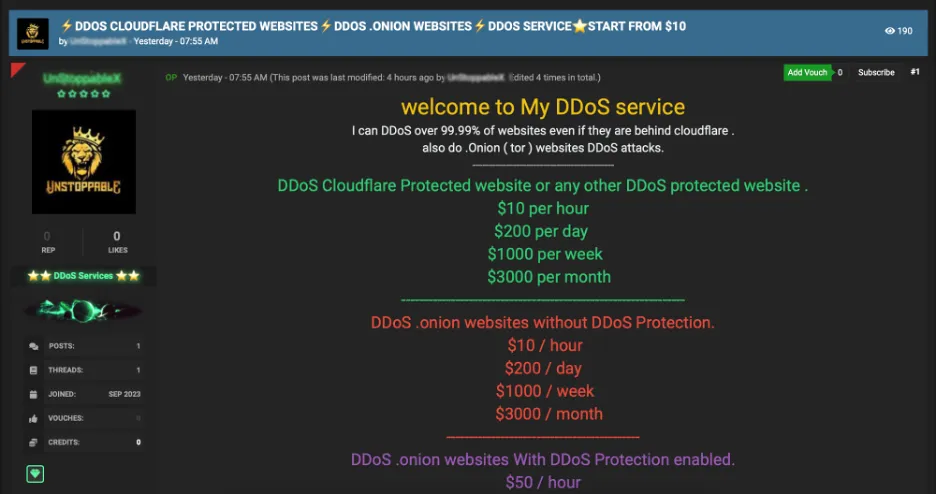
Photo: An image showcasing a DDoS as a Service offering on a forum
However, both types of services operate on a model akin to service by subscription (especially the first example), providing a degree of accessibility to anyone informed about where to find them, with the primary requirement being financial means.
Example 3: Stealers as a Service
Stealers as a Service is another category that encompasses tools designed to extract sensitive information like passwords, credit card numbers, and personal data. These tools are frequently used for identity theft and financial fraud. The accessibility of these tools heightens the risk for individuals and organisations since cyber criminals can readily acquire and deploy them to pilfer valuable information.
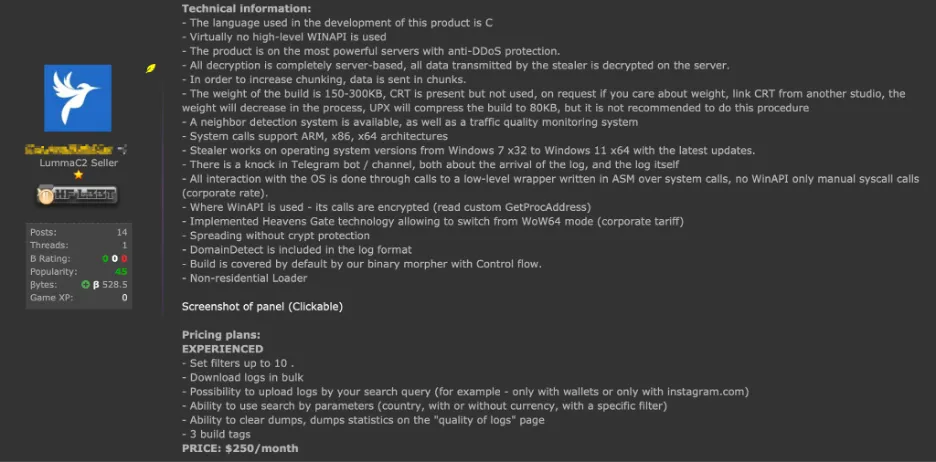 Photo: An image displaying the advertisement of LummaC2 Stealer
Photo: An image displaying the advertisement of LummaC2 Stealer
LummaC2 Stealer is a well-known example of this kind of service. It provides various features for capturing sensitive information, such as keylogging, form grabbing, and FTP stealing. It has a higher price point compared to some of the other software available, but perhaps not by a significant margin considering the potential return on value that cyber criminals could get from it.
Example 4: Phishing as a Service
Phishing as a Service is a subset of Cyber Crime as a Service, focusing on sending deceptive emails or messages to individuals to acquire sensitive information. Providers in this category offer an array of services, including tailoring phishing emails to appear legitimate and supplying detailed instructions on executing a successful phishing attack.
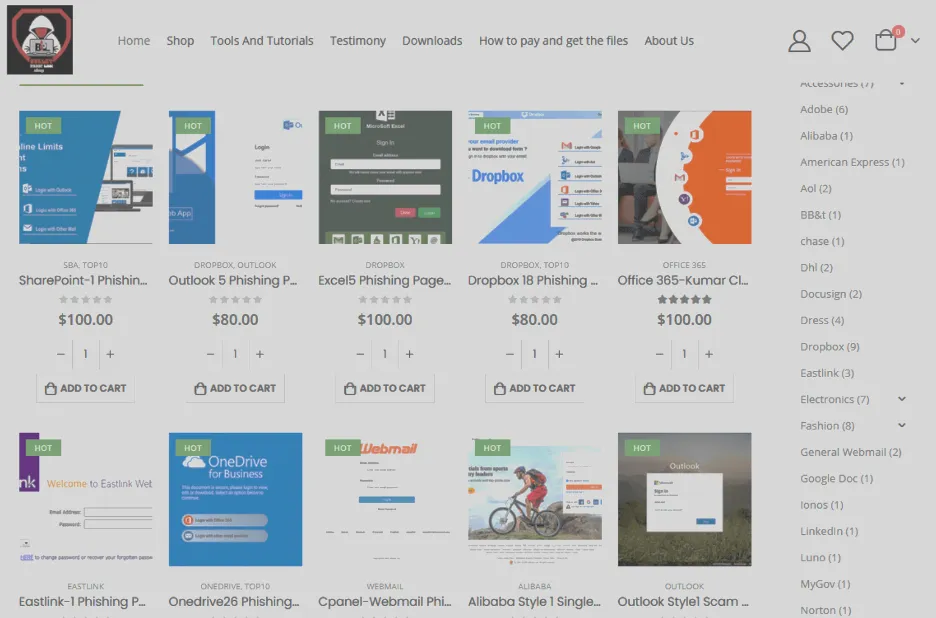 Photo: An image showcasing BulletProofLink templates
Photo: An image showcasing BulletProofLink templates
An example can be found above. The operators of BulletProofLink provide more than 100 templates and employ a highly adaptable business model. This model permits customers to purchase phishing pages and send emails independently. Alternatively, customers can fully leverage the service by using BulletProofLink’s hosted links where potential victims input their credentials.
Final Words
The rise of Cyber Crime as a Service has made it remarkably simple for anyone, regardless of technical expertise, to launch sophisticated cyber attacks. Within this sector, a wide range of services are available, including but not limited to ransomware, distributed denial of service, stealers, and phishing.
In this model, almost anything can be found, and the traditional concept of one-time payments is gradually diminishing.
While we have not extensively explored this, it is worth noting that customer support for these illicit services is often surprisingly efficient. Many sellers utilise platforms like Telegram to provide support, sometimes even surpassing the responsiveness of legitimate services. In certain cases, the support received from cyber criminals can exceed that of legitimate platforms.
Find Out How FractalScan Can Help You
To improve the visibility and defences around your organisation’s attack surface, try FractalScan’s attack surface management solution for free. With our Free account you can visualise the risks, track your cyber health score, and receive a summary report to demonstrate ROI to stakeholders.
Click here to get your Free FractalScan Surface account*
*Please note a business email is required for our Free account, as this will be used for your scan.





