
What is DORA?
The Digital Operational Resilience Act (DORA) establishes a unified ICT risk management framework for the EU financial sector, requiring the implementation of technical standards in ICT systems by January 17, 2025. The regulation aims to standardise risk management rules across the EU, ensuring consistent standards and strengthening the resilience of the EU financial system.
Who Does DORA Apply To?
DORA applies to a broad range of financial institutions within the EU, including banks, investment firms, credit institutions, crypto-asset service providers, and crowdfunding platforms. It also covers third-party service providers that offer ICT systems and services to financial firms, such as cloud services and data centres.
What Are the Requirements?
DORA focuses on five main pillars:
- ICT risk management
- Incident reporting
- Digital operational resilience testing
- ICT third-party risk management
- Information sharing
Financial entities are required to establish a clear risk management framework, perform regular risk assessments, conduct thorough testing, maintain incident response capabilities, and effectively manage third-party cyber risks.
What Are the Penalties?
Non-compliance with DORA can result in fines of up to €10 million or 5% of the total annual turnover, whichever is greater. Other consequences include enforced corrective actions, public reprimands, withdrawal of authorisation, and compensation for damages.
Attack Surface Management Can Help With DORA
Attack Surface Management (ASM) platforms include features that are consistent with and support DORA's requirements. For example, ASM solutions facilitate continuous asset discovery and management, which ensures complete visibility and management of all internet-facing assets, such as subdomains, IP addresses, and certificates.
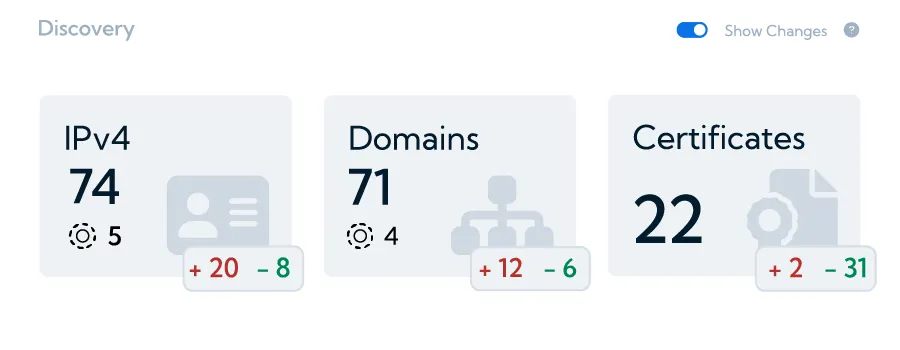
This feature contributes to maintaining an accurate and up-to-date inventory, which is important in identifying and managing risks associated with each asset, laying the groundwork for a strong ICT risk management framework as required by DORA.
DORA states that financial organisations must “establish, maintain and review a sound and comprehensive digital operational resilience testing programme as an integral part of the ICT risk-management framework.”
ASM solutions often provide real-time alerting and incident analysis, which directly supports DORA’s requirement for “reporting of major ICT-related incidents and notifying, on a voluntary basis, significant cyber threats to the competent authorities.”
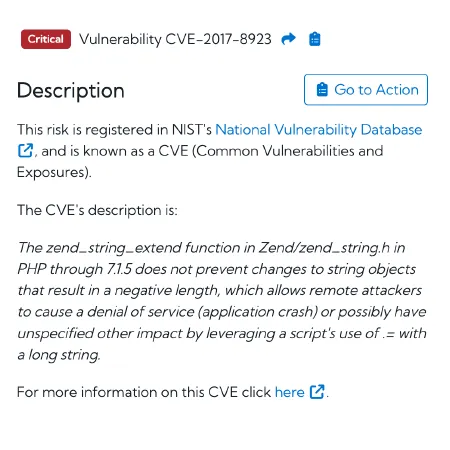
This feature provides immediate notifications and detailed analysis of potential security incidents, such as newly discovered vulnerabilities (CVEs) or exposed sensitive data, allowing for faster response and accurate incident reporting to authorities. This ensures that financial entities meet DORA's incident reporting obligations in a timely and effective manner.
ASM platforms typically include vulnerability detection and prioritisation systems that automate vulnerability scanning and prioritise issues according to severity using a scoring system.
This capability is crucial for comprehensive digital operational resilience testing, as emphasised by DORA, which states the importance of “assessing preparedness for handling ICT-related incidents, of identifying weaknesses, deficiencies and gaps in digital operational resilience, and of promptly implementing corrective measures.”
Managing ICT third-party risk is another important aspect of DORA, which includes “key principles for a sound management of ICT third-party risk.”
Many ASM solutions offer monitoring capabilities that extend to third-party digital assets, ensuring that the security posture of third-party vendors meets appropriate standards. This provides visibility into the security of external partners and assists with the management of ICT third-party risk.
Lastly, DORA demands “information-sharing arrangements on cyber threat information and intelligence.” ASM platforms often generate detailed reports on an organisation’s cybersecurity posture, which can be shared with regulatory authorities and peers, encouraging a collaborative approach to information sharing.
Next Steps With FractalScan Surface
FractalScan Surface helps organisations meet DORA’s ICT risk management, incident reporting, resilience testing, vendor management, and information sharing obligations by providing continuous asset monitoring, real-time incident alerts, automated vulnerability scanning, third-party risk assessments, and reporting capabilities.
Don’t risk noncompliance penalties — click here to get started with FractalScan Surface and ensure your organisation meets all DORA requirements by the January 2025 deadline.





