Introduction
We recently co-hosted a webinar on cyber security in the legal sector with our partners at CloudGuard, and thought it would also be a good topic for a blog. We’ll cover much of the same here: why is the legal sector such a target for attackers, what can we learn from previous incidents, and what does FractalScan tell us about their attack surfaces.
Juicy Targets
So why are organisations in the legal sector such a juicy target for attackers? There’s a number of reasons. Firstly, as many law firms are big multinational companies, they unsurprisingly suffer from many of the common issues that largely come from the difficulty of managing IT and accounts for a large number of people in many different locations.
On top of that, they have a number of things that make them good targets for attackers:
- They typically deal with lots of personal data, which attackers are always looking to steal.
- They deal with large amounts of money and in many cases, such as with Mergers and Acquisitions, handle large transfers of monies.
- They make use of technologies such as data rooms, which are third-party systems into which lots of sensitive data are copied and processed.
Whatever reasons attackers have for targeting them, the threats they face are broadly aligned with those of most organisations:
- Phishing and business email compromise.
- Ransomware attacks (which often start with phishing, of course).
- Insider threats, which mainly means mistakes such as misdelivery but does include malicious insiders.
Various people who focus on threat intelligence are reporting that legal companies are increasingly being targeted. In the UK, it’s prompted the National Cyber Security Centre to release this high-level guide on the threats they face.
Previous Incidents
In preparing for the webinar we did some quick research into previous cyber security incidents within the legal sector. Unfortunately, a quick Google finds lots of frightening stories.
More recently, the hack of CTS in late 2023 had a big impact on conveyancing and therefore house purchases in the UK. The root cause there was apparently the Citrix Bleed vulnerability.
Aside from CTS and some data breaches, the last few years have seen a string of ransomware incidents from all the big ransomware crews, including:
- November 2023: Allen and Overy hit by Lockbit.
- June 2023: Cl0p ransomware hits a number of firms, including Kirkland & Ellis, K&L Gates and Proskauer Rose, exploiting the MOVEIt FTA vulnerability.
- 2021: 4 New Square Chambers are hit by ransomware, and somewhat intriguingly get themselves an injunction against the attackers, which TheRegister was fairly skeptical about.
- 2017: DLA Piper are hit by the Petya ransomware.
The final example here is one of the big ones. Coverage on this incident has some terrifying details of what large-scale ransomware events mean to a company:
…an administrator, with administrator privileges, mistakenly clicked on an “update” to an accounting software that the Ukraine office used. This “update” was, in fact, a phishing scam that contained malware.
Despite the fact that DLA Piper’s cybersecurity team in Britain discovered the threat within 20 minutes, the virus nonetheless disabled the firm’s worldwide telephone system and most of its computer network. When employees came into work they were notified to not turn on any computer anywhere within the firm.
…DLA Piper paid over 15,000 hours of overtime to its IT department in attempting to restore the network
“Do Not Fall Down the Rabbit Hole of a Law Firm Data Breach”, Bigger Law Firm
What can we learn from these incidents? As in many incidents, it’s a lot of the same things:
- Protect your users from phishing with both technical (email protections, endpoint protections, MFA on all accounts) and non-technical defences (user training, fostering a culture where people are happy to ask for help and report something suspicious).
- Keep on top of your online attack surface, and make sure everything you have that’s connected to the internet is updated and maintained.
- Implement good practices for account management and administrator roles, such as enforcing separate accounts for privileged roles.
Example Attack Surfaces
To get an idea about how they’re doing from a cyber security perspective, we put some of the biggest law firms in the UK through FractalScan.
Email Configuration
Given the omminpresent threat of phishing and related attacks such as business email compromise, secure configuration of email records is crucial for all organisations, especially those in the legal sector.
The good news from our research is that all 24 of the biggest law firms in the UK have an SPF record in place, which is the minimum protection against email spoofing. Less impressive is that 6 of them either have no DMARC record, or do have a record but don’t have the policy field (p) set to do anything.
Scale
As with any large company, looking at some of the big legal companies we can quickly see how cyber security management gets harder with scale. Here’s an example from the FractalScan data - all the online assets we can discover for a single company plotted on a map:
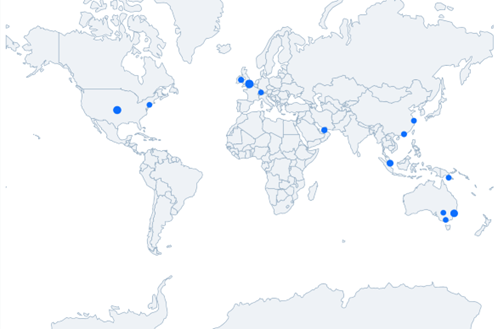
This included websites and cloud resources (on both AWS and Azure, in this case). How many IT teams do we think they have? At least three at a guess (US, Europe and the Middle East, and Asia-Pacific), but possibly more. Given this picture you can quickly understand how shadow IT and unmanaged assets are such a common problem for big, multinational companies; they’ve got lots of online assets, spread all over. This is why there’s so much value in finding and managing your external attack surface.
As another example, one of the companies we looked at had 640 websites. Think about what that means. Pretty much every one of them needs maintenance, from the webserver software to the framework and plugins, the TLS certificate and configuration, and the Content Security Policy and HTTP headers.
Typical Issues
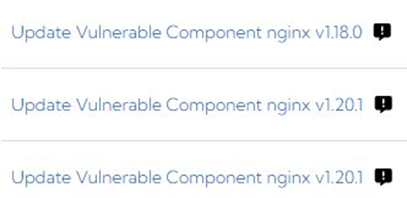
This problem of scale is also seen in the kinds of issues that FractalScan finds for these companies. We see unpatched and out of date webservers:
Plus a whole range of website issues. One company has 48 websites with expired certificates:
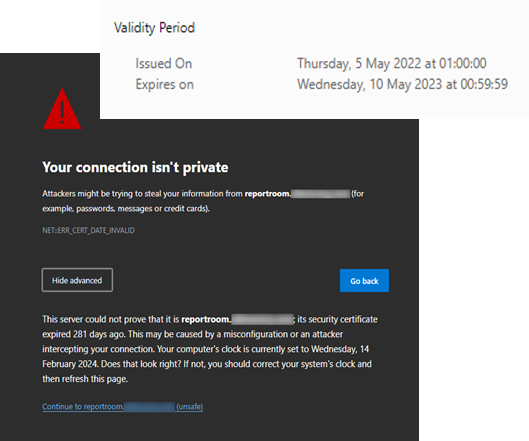
Best case, these are decommissioned websites than haven’t been properly taken down. But there’s always a chance they’re customer websites storing customer data. If the TLS certificate is lapsed then we can normally assume the website also needs patching and updating.
What You Can Do
These issues aren’t limited to the legal sector and anyone who has systems connected to the internet would benefit from understanding the make-up of their attack surface and overall exposure to risk! Take the first steps in securing your attack surface and identifying where your vulnerabilities lie.
Register for our FractalScan Surface free account and get a snapshot of your attack surface today.





