
Introduction
Our last blog on “What Is an Attack Surface?” covered what we mean by an online attack surface. Knowing what makes up your attack surface is the sensible first step, but then you have to start keeping on top of it. In this follow-up we provide an overview of one approach to managing an attack surface.
Here’s one way of thinking about attack surface management (asm), not as a singular task, but as an ongoing process:
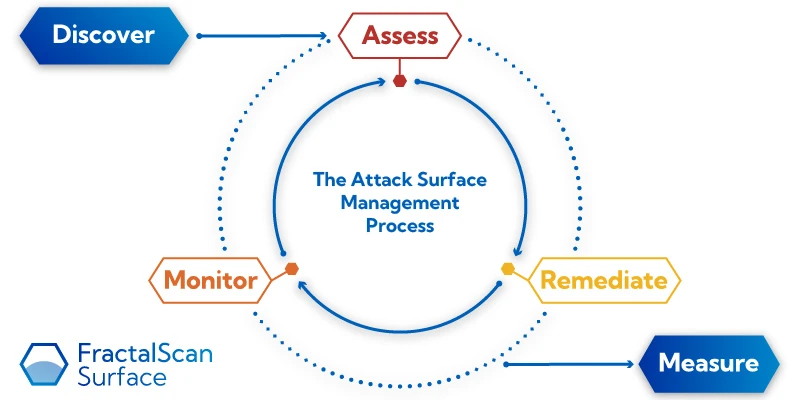
First we discover the assets that go into the process, which is a continual cycle of assessing assets for potential issues, remediating them, and monitoring for further changes. All the while discovering new assets, and measuring our progress. Below we’ll look at each element of this process in turn.
Step 1: Discovery and mapping
The first part of management is understanding the assets for which you are responsible. This requires determining every online asset that constitutes a part of, or connects to, your infrastructure. An audit needs to capture every asset and then appropriately define, label and record it.
An asset could be: a website, web app, certificate, service, software, computer, IP address, domain, URL, CDN, network device, API, cloud storage, database or mobile app to name but a few.
The potential scale, diversity and dynamic nature of your assets means that the use of asset inventories is often impractical. For your external attack surface this exercise must be done from the outside looking in, discovering all Internet-facing assets, whether they are known or unknown to you. This discovery process needs to be conducted as if you are the attacker with no prior knowledge, rather than the defender.
When you start analysing your infrastructure in detail, the amount of data involved can quickly become overwhelming. In addition to the assets, the relationships (or paths) between them also need to be captured to ascertain a useful, accurate model of how it all works.
An effective tool will require the user to enter a small amount of information, and leave the discovery of all the related and subsidiary components to the attack surface management tool.
Gaining accurate visibility of your attack surface provides you with the knowledge to reduce or mitigate the risks. This might include removing assets that are no longer used or needed. Gaining this knowledge enables you to regain control of your infrastructure such as removing any shadow IT infrastructure; infrastructure that has been setup within the company without authorisation. Other examples of assets that can be removed include accessible administration panels to databases, applications or e-mails in addition to removing unused ports such as FTP, RDP and SSH ports.
Once you know what you have, you can start looking after what you’ve got.
Step 2: Assessment
Once the attack surface has been discovered and classified, it needs to be assessed. This requires assessing each individual asset for any weaknesses and vulnerabilities. This requires plenty of thought and understanding for every asset. Each asset’s nuances need to be considered whilst constantly cross checking the very latest open-source threat intelligence. Our attack surface management solution FractalScan Surface, achieves this using a dynamic set of worker agents to carry out all the analysis.
For instance, if a certificate is being validated, we need to check that its signature is valid, that its configuration matches its intended purpose and that the cryptographic algorithms used are of a required standard. If a DNS entry is an email record, the record is assessed for misconfigurations that could potentially allow phishing e-mails to appear as though they come from your company when in fact they have come from an attacker. Any out-of-date software needs to be checked for vulnerabilities.
For every weakness or vulnerability present in an asset, we assign a relative severity so they can be prioritised. The severity is a measure of the risk if the vulnerability is not fixed. If an attack surface management tool can provide high level overall scores, this can be a huge benefit for the stakeholders that need concise information.
Step 3: Remediation
People responsible for the development, maintenance and support of online systems are not necessarily experts in cyber security, so providing useful remediation advice is a necessity in enabling the issue to be resolved quickly and efficiently. When the data has been collected and analysed, and vulnerabilities discovered, an attack surface management tool needs to display the pertinent information so the right resources can be assigned to resolve any risks quickly and effectively.
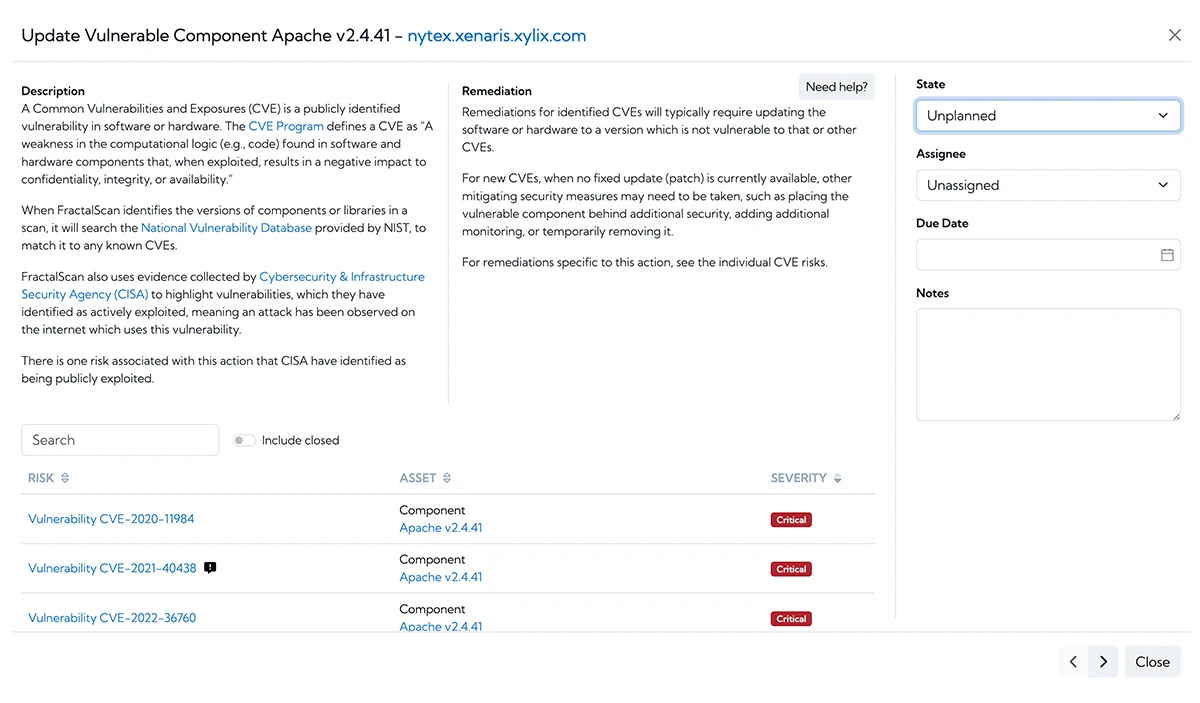
The team responsible for updating the infrastructure need to move fast. They need to work together and to make sure that the work is effectively divided between them. They need to be assigned risks and the progress of their risks tracked.
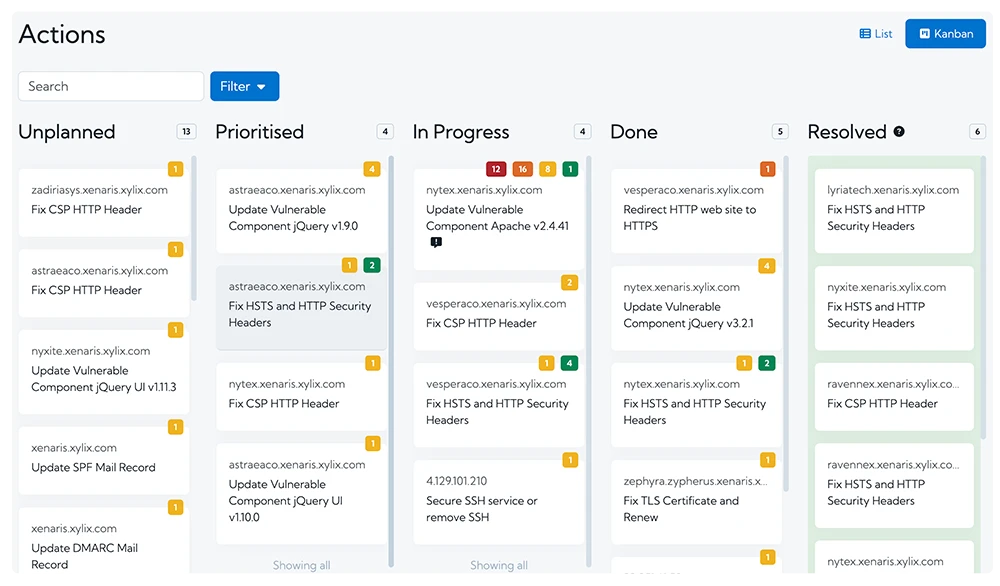
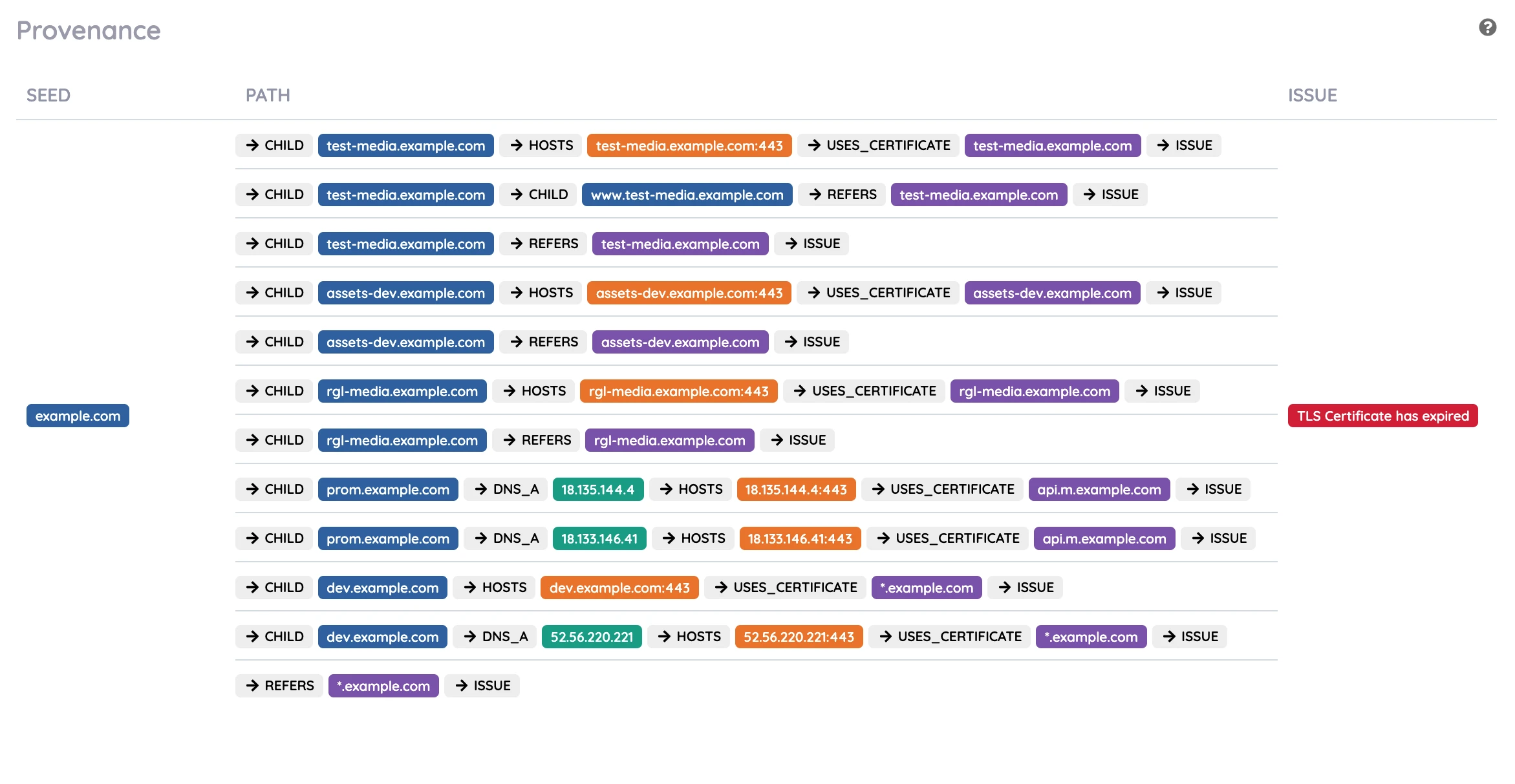
When remediating issues, an attack surface management tool should enable the issues to be understood easily, to be located within your infrastructure, and provide remediation advice. By providing unrestricted access to all the collected data, in an intuitive and user-friendly display, a risk can be fixed quickly and effectively. The attack surface management tool also needs to display the provenance of any issue, so the origin of the issue can be determined. This may identify common bad points, which enable the resolution of multiple issues at once.
Step 4: Monitoring
Unfortunately, cyber security is never finished. Once the attack surface has been mapped and assessed, it needs to be continually monitored. This requires running the discovery phase repeatedly and performing the assessment again. This way any new vulnerabilities or unexpected changes in the attack surface can be notified to the user. Any newly published vulnerabilities need to be found and remediated quickly before the eager attacker can run their script to find the weakness and exploit it.
Step 5: Measure
At a high level, the managers, CIOs, CTOs, and CISOs need to have accurate, succinct metrics to help them understand and prioritise the requirements and resource accordingly.
FractalScan Surface provides high level scores and metrics, and allows you to export the raw data or generate PDF summary reports.
How to do all of this?
As you can see the roles of attack surface management solution are broad, intensive, and detailed. All steps require high performance computing, analysis, and execution. The data needs to be in-depth and accurate. What’s more, this is not a one time job. The process needs to be automated so it can be repeated again and again.
FractalScan Surface performs all these tasks for your online infrastructure, simply by entering your domain names (yourcompany.com) or any known IP addresses.





